Jamf Account SSO and Reversed Names from Entra
Jul 28, 2025
While setting up Jamf Account SSO (not to be confused with Jamf Pro SSO), I ran into trouble with our Entra names and how Jamf handles them:
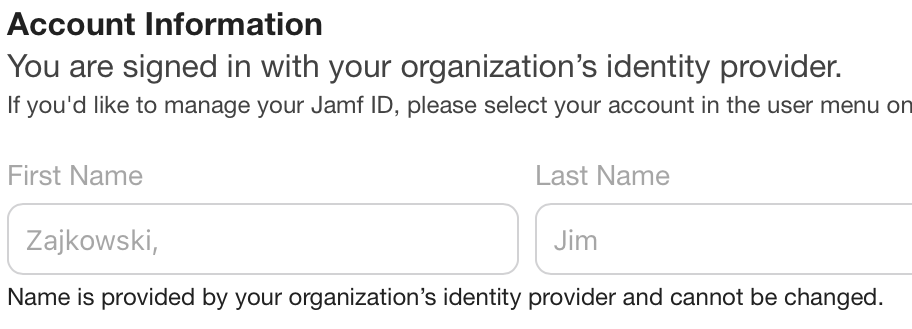
The issue is our Entra accounts all come from AD sync, and in general, AD puts people names in Family, Given order. Jamf Account SSO - although configured for first and last names, seems to take the full name field, split on the first space, and assume it’s in US-centric Given Family order.
The workaround was provided to me across a few Jamf support sessions.
Follow the Jamf Account setup process first
- Follow Jamf’s guide to get the basics set first.
Create an additional attribute in Azure
- Find the Entra
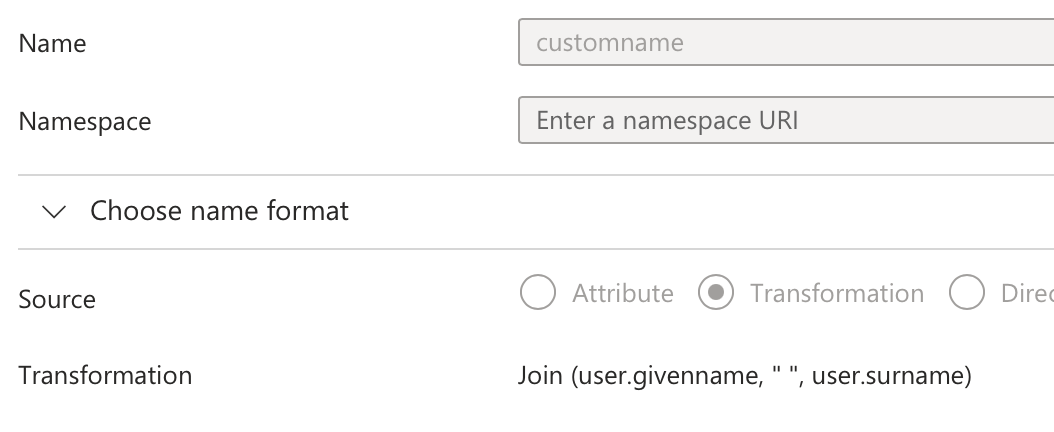
Enterprise Applicationfor Jamf Account. Single Sign OntabAttributes and Claims- Click
Edit Add new Claim- Name it something like
customname(you will need this name, below) - Create a Transformation of
Join, joininguser.givenname," ", anduser.surname.
- Flip over to the App Registration in Entra
- Click on
Manifestunder theManageheading - Change the
acceptMappedClaimstotrue - While in App Registration, create a new secret for the app.
- Copy the
Application IDandDirectory IDfrom the App’s Overview.
Change from the Entra connection to Generic OIDC
- In Jamf Account, create a new SSO provider.
- Use Generic OIDC.
- Enter the Client ID and secret from before.
- For Issuer URL, use the same
Authority URL - Click Save
- Turn on Advanced Features (Jamf Account > Organization > Settings)
- Go back to the SSO configuration. You should now see a
Custom mappingsection. Set it like this. If you used a different name thancustomnamechange it above.
Groups are TBD
1{
2 "mapping_mode": "use_map",
3 "userinfo_scope": "email openid profile",
4 "attributes": {
5 "name": "${context.tokenset.customname}",
6 "email": "${context.tokenset.preferred_username}",
7 "groups": "${context.tokenset.groups}",
8 "username": "${context.tokenset.preferred_username}",
9 "federated_groups": "${context.tokenset.groups}",
10 "federated_locale": "${context.tokenset.locale}",
11 "federated_zoneinfo": "${context.tokenset.zoneinfo}"
12 }
13}